BitViraj Technologies - Your Gateway to
Tomorrow's Innovations

Lattice-Based Cryptography: Design, Analysis, and Prototyping of Post-Quantum Cryptographic Schemes
Executive Summary
Lattice-based cryptography has emerged as a cornerstone of post-quantum cryptography (PQC), offering strong security guarantees against both classical and quantum adversaries. As quantum computing advances threaten traditional cryptographic systems, lattice-based schemes stand out due to their solid theoretical foundations, versatility, and real-world performance.
This article provides a comprehensive exploration of lattice-based cryptography—from mathematical underpinnings to real-world deployment. We examine foundational hard problems such as Learning With Errors (LWE) and Short Integer Solution (SIS), discuss cryptographic design principles, security analysis, and implementation considerations, and analyze standardized schemes such as CRYSTALS-Kyber and CRYSTALS-Dilithium, selected by NIST for post-quantum key exchange and digital signatures.
As governments, enterprises, and blockchain ecosystems prepare for the quantum era, understanding lattice-based cryptography is no longer optional—it is essential.
Introduction: Why Post-Quantum Cryptography Matters
The prospect of large-scale quantum computers poses an existential threat to today's public-key cryptography. Shor's algorithm demonstrates that quantum machines can efficiently break:
RSA
Diffie–Hellman
Elliptic Curve Cryptography (ECC)
This vulnerability has catalyzed the development of post-quantum cryptography, cryptographic systems designed to remain secure in a quantum world.
Why Lattice-Based Cryptography Stands Apart:
Conjectured quantum resistance (no known efficient quantum attacks)
Worst-case to average-case security reductions
Versatility (encryption, signatures, homomorphic encryption)
Competitive performance and scalability
Recognizing these strengths, NIST selected CRYSTALS-Kyber and CRYSTALS-Dilithium as primary post-quantum standards—marking a historic shift in global cryptographic infrastructure.
Mathematical Foundations of Lattices
A lattice is a discrete subgroup of ℝⁿ formed by integer linear combinations of basis vectors.
Formally, given linearly independent vectors b₁,b₂,…,bₙ ∈ ℝⁿ, the lattice L(B) is:
L(B) = {∑i=1n xᵢ bᵢ | xᵢ ∈ ℤ}
Determinant (det(L))
Measures the volume of the fundamental parallelepiped.
Shortest Vector (λ₁(L))
Length of the shortest non-zero lattice vector—central to cryptographic hardness.
Covering Radius (μ(L))
Maximum distance from any point in space to the nearest lattice point.
Cryptographic security arises from the fact that the same lattice can have many bases. A "bad" public basis hides structure, while a "good" private basis enables efficient computation.
Core Lattice-Based Hard Problems
Shortest Vector Problem (SVP) & Closest Vector Problem (CVP)
SVP
Find the shortest non-zero vector in a lattice.
CVP
Find the lattice vector closest to a target point.
Both are NP-hard in the worst case and form the foundation of lattice cryptography's security assumptions.
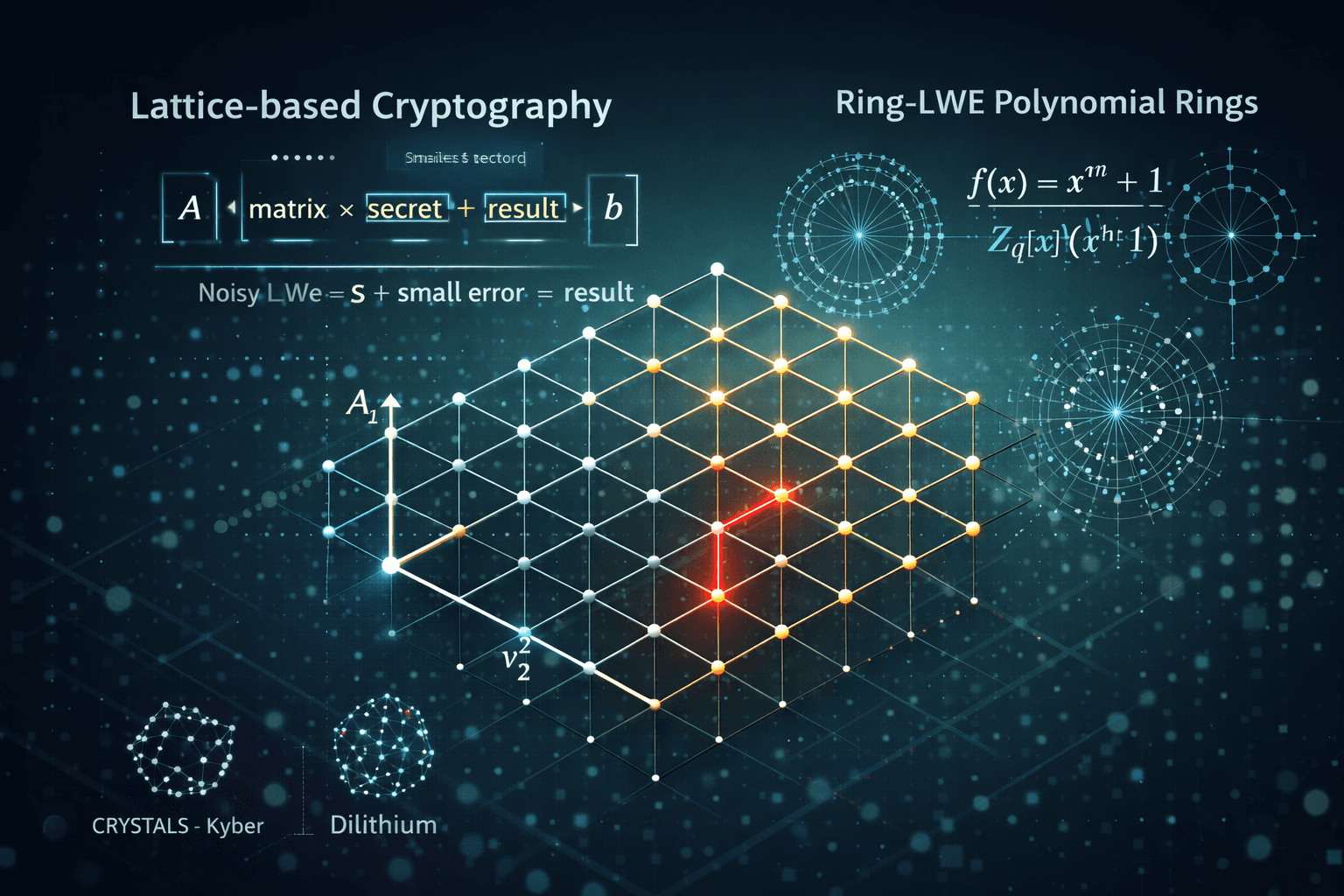
Learning With Errors (LWE)
Introduced by Oded Regev, LWE is the backbone of modern lattice cryptography.
Given matrix A, secret s, and small error e:
b = As + e (mod q)
The challenge is distinguishing noisy linear equations from random data.
Why LWE matters:
- Provable reduction from worst-case lattice problems
- Resistant to known quantum attacks
- Strong theoretical guarantees
Ring-LWE and Module-LWE
Ring-LWE
- Compact keys
- Fast polynomial arithmetic
Module-LWE
- Balance between performance and security robustness
- Used in Kyber and Dilithium
Module-LWE mitigates some concerns around ideal lattice structures while retaining efficiency.
Short Integer Solution (SIS)
Given matrix A, find a short vector x such that:
Ax = 0 (mod q)
SIS underpins:
- Digital signatures
- Collision-resistant hash functions
Lattice-Based Cryptographic Schemes
Public-Key Encryption & Key Encapsulation
Regev's LWE Encryption
- ✓Strong theoretical security
- ✗Impractical key and ciphertext sizes
NewHope (Ring-LWE)
- ✓Efficient polynomial arithmetic
- ✓Compact keys and ciphertexts
- ✓Influenced modern standardization efforts
CRYSTALS-Kyber (NIST-Selected KEM)
Kyber is the flagship post-quantum key exchange standard.
Key features:
- Based on Module-LWE
- IND-CCA2 security via Fujisaki–Okamoto transform
- Efficient across software and hardware platforms
| Security Level | Module Dimension | Ciphertext Size |
|---|---|---|
| Kyber-512 | 2 | ~1088 bytes |
| Kyber-768 | 3 | ~1184 bytes |
| Kyber-1024 | 4 | ~1568 bytes |
Digital Signatures
CRYSTALS-Dilithium (NIST Standard)
A Fiat–Shamir-based signature scheme using Module-LWE/SIS.
- ✓Strong EUF-CMA security
- ✓Deterministic signing
- ✓Simple and robust implementation
Signature sizes: ~1387 bytes (Level 2) to ~2701 bytes (Level 5)
Falcon (NTRU-Based)
- ✓Extremely compact signatures (~666 bytes)
- ✓High performance
- ⚠More complex implementation
- ⚠Uses ideal lattices, raising long-term security discussions
Security Analysis & Parameter Selection
Concrete Security
Attacks rely on BKZ lattice reduction, whose complexity grows exponentially with block size β.
Modern estimators evaluate:
Primal attacks
Dual attacks
Hybrid strategies
Quantum Resistance
Current Status
- No known polynomial-time quantum algorithm for SVP/LWE
- Grover's algorithm offers only quadratic speedup
- Parameters can be scaled accordingly
Assessment:
Quantum resistance remains heuristic but strongly supported by current research.
Implementation & Prototyping Considerations
Number Theoretic Transform (NTT)
Function
Enables fast polynomial multiplication
Performance Gain
Reduces complexity from O(n²) → O(n log n)
Importance
Critical for performance in Kyber and Dilithium
Error Sampling
Centered binomial distributions replace costly Gaussians:
X = ∑(bᵢ - bᵢ')
Efficient
Secure
Hardware-friendly
Hardware & Side-Channel Resistance
FPGA/ASIC
High throughput implementations
Constant-time
Mandatory execution
Masking
Protection against side-channels
Rejection-sampling
Essential security measure
Ongoing Research Challenges
Ideal lattice quantum vulnerability
Reducing ciphertext and signature sizes
Improving efficiency for constrained devices
Ensuring cryptographic agility as standards evolve
Practical Deployment Strategies
Hybrid Cryptography
Combine classical (ECDH) and post-quantum (Kyber):
Immediate Protection
Quantum protection today
Compatibility
Backward compatibility
Feasibility
Proven feasibility (e.g., Google CECPQ2)
Defending Against "Harvest Now, Decrypt Later"
Organizations should migrate now, especially for:
Financial systems
Healthcare data
National infrastructure
Conclusion
Lattice-based cryptography has evolved from academic theory to production-grade security infrastructure. With strong mathematical foundations, demonstrated quantum resistance, and global standardization momentum, schemes like CRYSTALS-Kyber and CRYSTALS-Dilithium are poised to secure the future of digital communication.
For enterprises, blockchain platforms, fintech innovators, and governments, early adoption of lattice-based cryptography is not just prudent—it is a strategic advantage.
At Bitviraj Technology, we view post-quantum readiness as a core pillar of next-generation digital trust.
Case Studies
Empowering Digital
Evolution
Blogs
Empowering Digital
Evolution
BitViraj Technologies - Your Gateway to
Tomorrow's Innovations
Embark on a DigitalJourney


The next-generation digital technology company Bitviraj has the potential to empower and reinvent business in the current fast-paced market.
Our Service
- Website Development
- Application Development
- Blockchain Development
- Gaming and Metaverse