BitViraj Technologies - Your Gateway to
Tomorrow's Innovations

The Privacy Trinity: A Research on the Convergence of MPC, FHE, and Zero-Knowledge Proofs for the Next Era of Trustless Computation
Privacy-preserving computation is undergoing a structural transformation. Once seen as academic curiosities, Multi-Party Computation (MPC), Fully Homomorphic Encryption (FHE), and Zero-Knowledge Proofs (ZKPs) have matured into practical technologies capable of securing global financial infrastructure, collaborative artificial intelligence, and next-generation blockchains.

By Bitviraj Technology
The Privacy Trinity Convergence

The Privacy Trinity: A Research on the Convergence of MPC, FHE, and Zero-Knowledge Proofs for the Next Era of Trustless Computation
Overview
Privacy-preserving computation is undergoing a structural transformation. Once seen as academic curiosities, Multi-Party Computation (MPC), Fully Homomorphic Encryption (FHE), and Zero-Knowledge Proofs (ZKPs) have matured into practical technologies capable of securing global financial infrastructure, collaborative artificial intelligence, and next-generation blockchains.
Far from competing cryptographic approaches, these three primitives are increasingly understood as cooperative components of a unified architecture.
This study examines the modern capabilities, limitations, and engineering patterns surrounding MPC, FHE, and ZKPs, highlighting how their convergence can deliver secure, private, and verifiable computation at scale. It also analyzes the emerging hybrid privacy stack shaping real-world systems, from encrypted smart contracts to trust-minimized AI pipelines. The result is a forward-looking perspective on how cryptography is evolving to meet regulatory challenges, economic demands, and the expectations of a digitally interconnected society.
Introduction
The past decade has seen an explosion of data, computation, and distributed systems. Every business now faces the same paradox:
Data is essential for
• Analytics
• Personalization
• Automation
Data exposure is catastrophic
• Legal consequences
• Competitive risks
This tension is amplified by the rise of public blockchains, federated AI, cross-institutional data economics, and privacy regulations such as GDPR and HIPAA.
Traditional access control or encryption-at-rest models are no longer sufficient. The modern challenge is not just protecting data but enabling meaningful computation on data without compromising privacy.
In response, a new cryptographic model is emerging - one where privacy is not a limitation but a programmable feature.
The primary drivers of this shift are:
Multi-Party Computation (MPC)
Fully Homomorphic Encryption (FHE)
Zero-Knowledge Proofs (ZKPs)
Individually, each solves a different aspect of the privacy challenge. Together, they form a coherent "privacy trinity" capable of powering an encrypted yet functional digital ecosystem.
Background
Privacy-preserving computation is no longer the domain of niche cryptographers.
It has become a strategic priority for:
Banks
Like J.P. Morgan, which use MPC for secure fraud analysis across institutions.
Healthcare Systems
Like UC San Diego Health, exploring encrypted multi-center research on patient data.
AI Companies
Like Meta, navigating regulatory and competitive concerns over training data.
Blockchain Platforms
Like Ethereum, building confidential smart contracts and scalable rollups with ZKPs.
Enterprises
Aiming to reduce liability and exposure while maintaining analytical value.
The demand is clear: computation must move to the data, not the other way around - and it must do so without exposing the data.
Fully Homomorphic Encryption: The Private Cloud Computer
Fully Homomorphic Encryption (FHE) allows arbitrary computation on encrypted data. Once encrypted under an FHE scheme, data can be processed indefinitely without revealing the underlying plaintext to the compute node.
Non-interactive
The server performs all work independently
Encrypted-in, encrypted-out
The server never sees plaintext
Functionally expressive
Supports addition, multiplication, and arbitrary circuits
Real-World Applications
Encrypted Smart Contracts
Projects like Zama's fhEVM and Fhenix are building blockchains where all contract logic operates over ciphertext.
Fact: Zama's fhEVM allows a user to confidentially vote on a DAO proposal or trade an NFT without revealing their choice or identity to the public ledger.
Privacy-Preserving AI
Companies like PrivaSea use FHE for encrypted ML inference.
Example: A hospital could send encrypted medical scans to a cloud AI. The AI analyzes the scans for tumors and returns an encrypted diagnosis ("high risk" or "low risk") without ever decrypting the sensitive image.
Confidential Cloud Services
Google's Fully Homomorphic Encryption Transpiler project aims to make FHE accessible to developers, allowing them to run standard C++ code on encrypted data in the cloud.
Limitations
High computational cost: Ciphertexts can be ~10,000x larger than plaintexts
Bootstrapping overhead: Necessary noise management slows down complex computations
Hardware requirements: Real-time usage often requires specialized hardware (e.g., GPUs, FPGAs)
Specialized hardware requirements for real-time usage
These constraints make FHE extremely powerful but currently best suited for controlled, high-value workloads.
Zero-Knowledge Proofs: The Verifiable Compute Layer
ZKPs let one party prove that a computation was executed correctly without revealing the inputs, the program, or any intermediate values. In the context of privacy-preserving systems, ZKPs serve as the verification layer.
Key Capabilities:
Verifiability without transparency
Succinctness (especially SNARKs)
Transparency (in STARKs)
Low-cost verification
Real-World Applications & Facts:
zkFHE: Verifying Homomorphic Computation
FHE alone cannot prove correctness. To solve the "trust in the compute node" problem, systems can run the computation with FHE and generate a ZK proof that it was performed correctly.
Example: A dark pool trading system using FHE to match orders could use a ZKP to prove to regulators that no illegal front-running occurred, without revealing the trades.
ZK Rollups
Platforms like zkSync, StarkNet, and Scroll use ZKPs to bundle thousands of transactions into a single proof.
Fact: Polygon zkEVM processes over 1,000 transactions per second by submitting a single, tiny proof to Ethereum, reducing costs by ~90%.
Private Identity
The Worldcoin project uses ZKPs to verify a user's uniqueness (via iris scan) without storing or revealing their biometric data.
Limitations:
Proof generation is expensive
Can require significant memory and time for large circuits
Circuit complexity
Designing and optimizing ZK circuits is a highly specialized skill
Trusted setup
Some ZK systems (SNARKs) require a one-time trusted setup ceremony
zkFHE: Verifying Homomorphic Computation
FHE alone provides confidentiality but cannot prove that the compute node executed the function correctly. It solves the privacy problem but not the trust problem.
This is where ZKPs complete the picture. Systems can:
Run the computation with FHE on the encrypted data
Generate a ZK proof that the homomorphic operations were performed according to the agreed-upon circuit or program
Return both the encrypted result and the proof to the user
This powerful synergy merges confidentiality and verifiability.
Example:
A dark pool trading engine could use FHE to match buy and sell orders encrypted under a shared key. A ZKP could then be generated to prove to all participants and regulators that the matching was executed fairly (e.g., following a price-time priority rule) without revealing the individual orders, preventing illegal front-running.
ZK Rollups: The Scalability Engine for Blockchains
ZK Rollups are the most prominent and successful application of ZKPs today. Platforms such as zkSync Era, StarkNet, Polygon zkEVM, and Scroll bundle thousands of transactions off-chain and then submit a single, small validity proof to the underlying layer (like Ethereum).
High Throughput
By processing transactions off-chain, they can achieve thousands of transactions per second (TPS).
Fact: StarkNet has demonstrated peaks of over 200 TPS, a massive improvement over Ethereum's ~15-30 TPS.
Lower Costs
The cost of verifying a single proof for a batch of transactions is distributed among all users, dramatically reducing individual transaction fees.
Strong Security Guarantees
The security of the rollup inherits from the underlying blockchain, as the ZKP ensures that the new state is valid.
Private Identity & Credentials: The End of Oversharing
ZKPs are revolutionizing digital identity by enabling selective disclosure. Systems can verify a credential without seeing it.
Proving Age
A user can prove they are over 18 from a digital driver's license without revealing their exact birth date or other personal details.
Proving Citizenship/Creditworthiness/Membership
A person can prove they are a citizen of a country to access a service, have a credit score above a threshold for a loan, or are a member of a DAO - all without exposing the underlying documents or data.
Fact: The Worldcoin project uses a custom ZKP (Semaphore) to allow users to prove they are a unique human (verified by an orb) without linking that proof to their iris scan or identity.
Limitations & Engineering Challenges
While ZKPs offer beautiful mathematical guarantees, they come with significant real-world hurdles that are the focus of intense research and development.
Proof Generation is Computationally Expensive
The prover's work is highly intensive, requiring powerful hardware (high-end GPUs, and soon, ASICs) and significant time, especially for complex computations. This can lead to centralization pressures around prover entities.
Large Circuits Become Difficult to Optimize
Translating arbitrary programs into ZK-friendly circuits (often using R1CS or AIR) is a specialized skill. Inefficient circuit design can lead to proof generation times and costs that are orders of magnitude higher than necessary.
Some ZK Systems Require a Trusted Setup
SNARKs, in particular, often rely on a "Trusted Setup Ceremony" to generate a common reference string (CRS). While these ceremonies (like the one for Zcash) are designed to be secure if at least one participant is honest, they introduce procedural complexity and a perceived "weak link." STARKs and other transparent systems are gaining popularity to avoid this.
In essence, ZKPs offer a verifiable compute layer, but the path to generating that verification is paved with complex engineering and hardware challenges that must be overcome for mass adoption.
Multi-Party Computation: The Trust-Minimized Collaborator
MPC allows multiple participants to compute a shared result without exposing individual inputs. Trust is distributed; no single party can compromise the system.
Strengths
Removes single points of failure
Ideal for multi-institution workflows
Proven useful for digital assets and custody
Real-World Applications & Facts:
Secure Wallet Signing
Custodians like Fireblocks and Coinbase use MPC to distribute private keys.
Fact: Fireblocks' MPC-CMP protocol ensures that a hacker would need to compromise a threshold of geographically distributed nodes to steal funds, making it exponentially more secure than a single private key.
MPC-Based Order Matching
A decentralized exchange (DEX) built on MPC can keep the order book private.
Example: The Enigma project pioneered this concept, allowing for fair trading without exposing orders to miners who could engage in Maximal Extractable Value (MEV) exploitation.
Confidential Salary Analysis
Several companies could use MPC to compute the industry's average salary for a specific role without any company revealing its own confidential payroll data.
Limitations:
High network overhead
Constant communication between parties creates latency
Vulnerability to slow nodes
The protocol's speed is limited by the slowest participant
Increased latency
Not ideal for real-time, low-latency applications
MPC shines in distributed trust scenarios but is not ideal for heavy computation without optimization.
The Case for a Hybrid Privacy Stack
A major insight emerging from industry is that no single technology solves everything.
Why Hybridization Is Necessary
Hybrid Privacy Stack Architecture
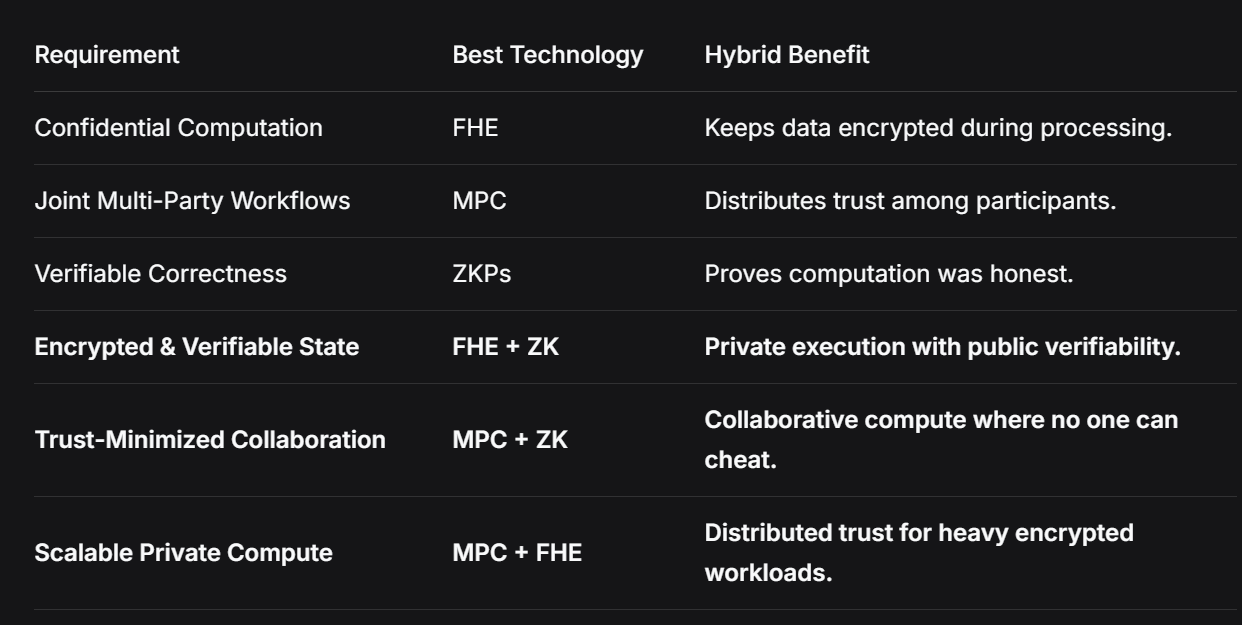
Real-World Hybrid Models:
FHE + ZK (zkFHE)
Ideal for encrypted smart contracts. A blockchain like Fhenix uses FHE for private state and ZKPs to verify the encrypted state transitions, ensuring both privacy and correctness.
MPC + ZK
Excellent for private governance. A DAO could use MPC to tally encrypted votes and a ZKP to prove the tally was correct without revealing individual votes.
MPC + FHE
Suitable for multi-organization AI. Several banks could use MPC to jointly create a shared FHE key, send their encrypted data to a cloud server, and let the server train a model on the combined encrypted dataset.
Industry Example: Octra
Companies such as Octra are experimenting with:
FHE-backed computation
Machine-learning-assisted consensus
ZK proofs for verification
MPC for collaboration
This signals a shift toward fully encrypted, verifiable compute networks.
Emerging Use Cases Across Industries
Finance & DeFi
• Private credit scoring for under-collateralized loans
• Encrypted dark pools
• MPC-secured institutional custody
Healthcare & Research
• Multi-hospital analysis of encrypted patient records
• Identify disease patterns without sharing sensitive data
Artificial Intelligence
• Training AI models on encrypted data from multiple competitors
• Enabling breakthroughs without violating antitrust or privacy laws
Public Blockchains
• Truly private NFTs
• Confidential DeFi positions
• Identity-shielded social media platforms on-chain
Social Media
• Newsfeed that ranks content based on encrypted preferences
• Ensures the platform "understands" you without building a detailed, exposed profile
We are moving toward a world where systems know what to do for you without ever knowing you.
Future Outlook: Toward an Encrypted World
The convergence of MPC, FHE, and ZKP marks the beginning of a new computational era.
Privacy will become:
Default, not optional
Programmable, not restrictive
Verifiable, not trust-based
We are heading toward an ecosystem where:
• Smart contracts run privately
• AI learns from encrypted datasets
• Financial infrastructures are trust-minimized
• Institutions cooperate without sharing raw data
• Identity becomes selective and user-controlled
Privacy is evolving from a defensive posture into an enabler of new products - unlocking data collaborations previously considered impossible.
Conclusion: The Inevitable Encrypted Future
MPC, FHE, and ZK are not separate technological roads.
They are three lanes of the same highway leading toward a world where:
Data can be used without being exposed
Computation can be trusted without transparency
Collaboration can be decentralized without sacrificing privacy
Enterprises, governments, and developers who embrace this cryptographic convergence will be positioned to build the next generation of trustworthy digital infrastructure.
Those who don't will struggle to operate in a world where privacy, security, and verifiability are no longer negotiable - they are simply expected.
The Privacy Trinity is not just a research topic. It is the foundation for the next era of the internet.
Case Studies
Empowering Digital
Evolution
Blogs
Empowering Digital
Evolution
BitViraj Technologies - Your Gateway to
Tomorrow's Innovations
Embark on a DigitalJourney


The next-generation digital technology company Bitviraj has the potential to empower and reinvent business in the current fast-paced market.
Our Service
- Website Development
- Application Development
- Blockchain Development
- Gaming and Metaverse






