BitViraj Technologies - Your Gateway to
Tomorrow's Innovations

By Bitviraj Technology
SSI HR Architecture Blueprint
Revolutionizing HR: A Self-Sovereign Identity (SSI) Architecture for Employee Lifecycle Management
How Decentralized Identity is Transforming Corporate HR Systems
Introduction
In today's digital workplace, managing employee identities has become increasingly complex and vulnerable.
Traditional systems rely on centralized databases that are prone to breaches, create administrative bottlenecks, and compromise employee privacy. Enter Self-Sovereign Identity (SSI)-a paradigm shift that empowers individuals with control over their digital identities while providing organizations with unprecedented security and efficiency.
This article explores a practical SSI implementation for employee management, complete with architectural insights and real-world applications.
The Problem with Traditional Employee Identity Management
Most organizations today struggle with:
Fragmented Identity Systems
Separate credentials for HRIS, email, project tools, and physical access
Manual Verification Processes
Repeated background checks and employment verification requests
Privacy Concerns
Employees' sensitive data stored across multiple vulnerable systems
Offboarding Challenges
Delayed revocation of access when employees leave
Compliance Overhead
Meeting GDPR, CCPA, and industry-specific regulations
Architectural Overview
SSI HR System Architecture
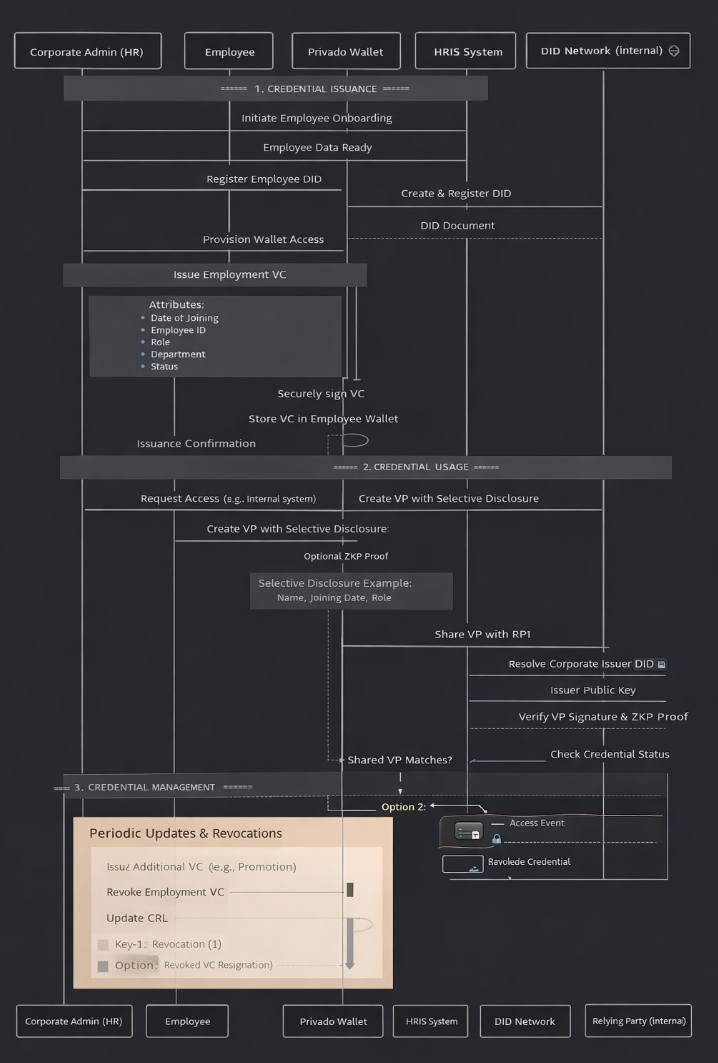
The SSI Solution: A Three-Phase Architecture Breakdown
Overview of All Stakeholders
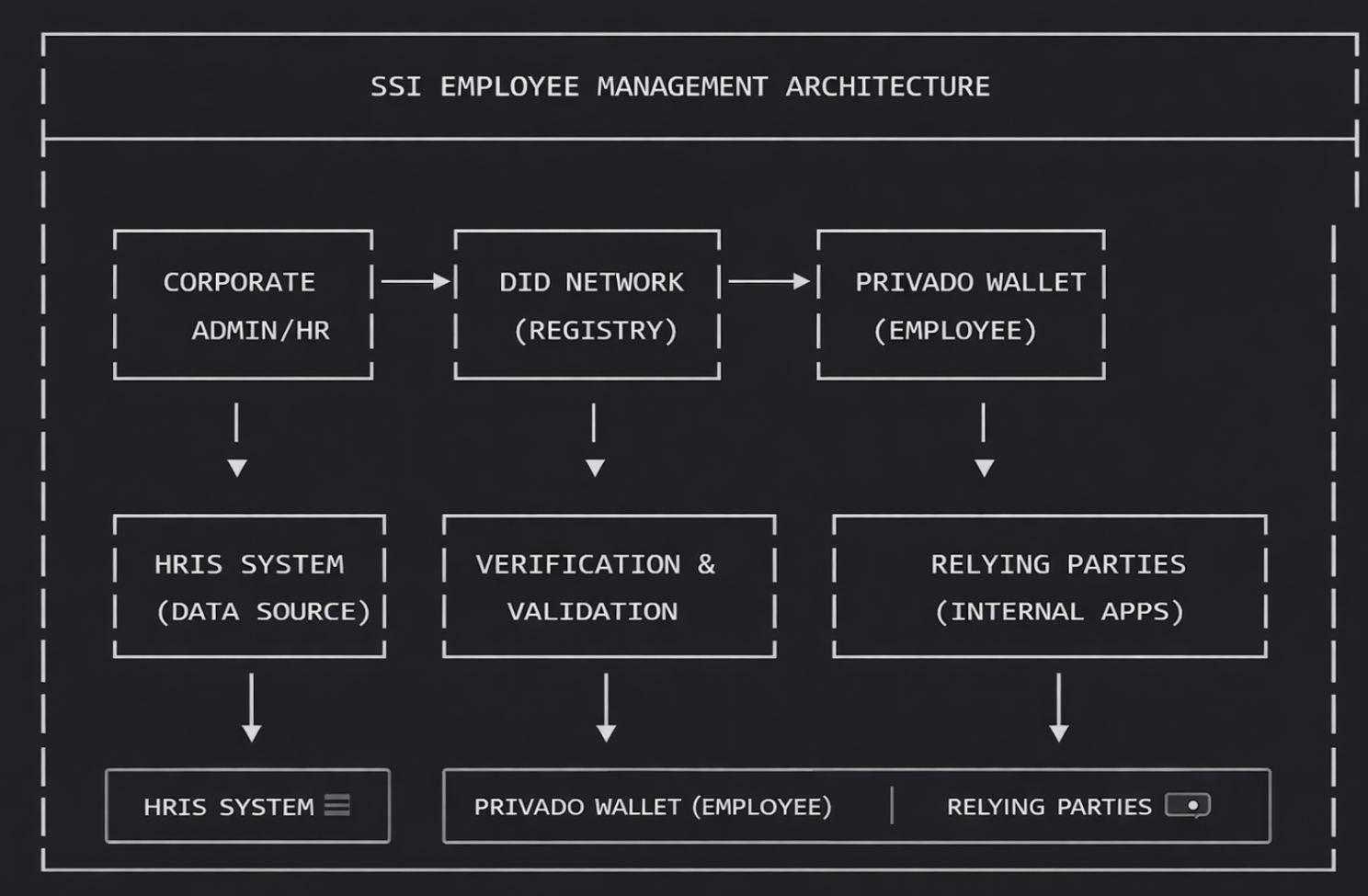
Technical Architecture
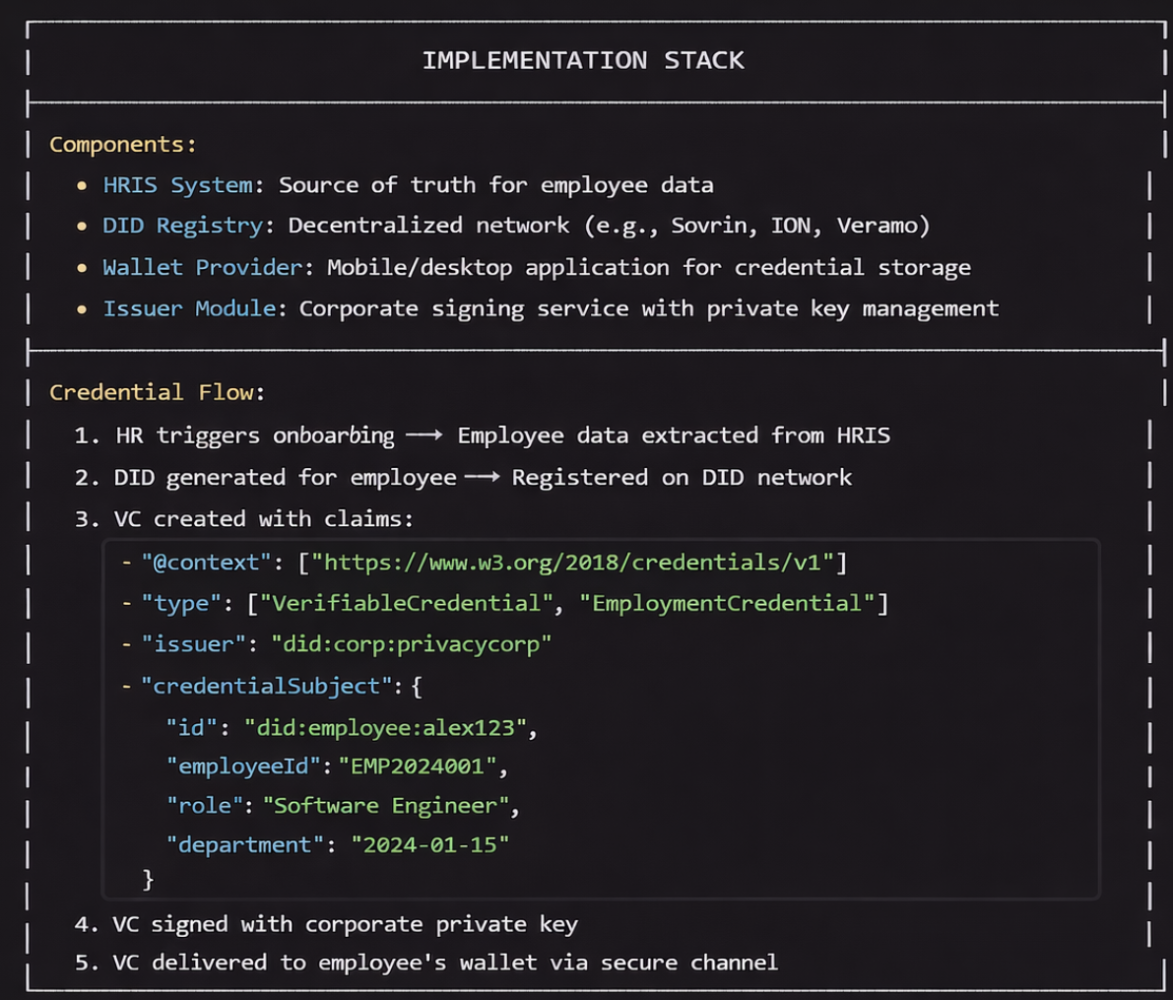
Components:
• HRIS System: Source of truth for employee data
• DID Registry: Decentralized network (e.g., Sovrin, ION, Veramo)
• Wallet Provider: Mobile/desktop application for credential storage
• Issuer Module: Corporate signing service with private key management
Flow:
HR triggers onboarding → Employee data extracted from HRIS
DID generated for employee → Registered on DID network
VC created with claims:
{
"@context": ["https://www.w3.org/2018/credentials/v1"],
"type": ["VerifiableCredential", "EmploymentCredential"],
"issuer": "did:corp:privacycorp",
"credentialSubject": {
"id": "did:employee:alex123",
"employeeId": "EMP2024001",
"role": "Software Engineer",
"department": "Engineering",
"joiningDate": "2024-01-15"
}
}VC signed with corporate private key
VC delivered to employee's wallet via secure channel
Innovation Point
The employee now holds a cryptographically verifiable digital employment certificate that they control, eliminating dependency on HR for every verification.
Phase 2: Credential Usage - Privacy-Preserving Verification
Privacy-Preserving Verification Architecture
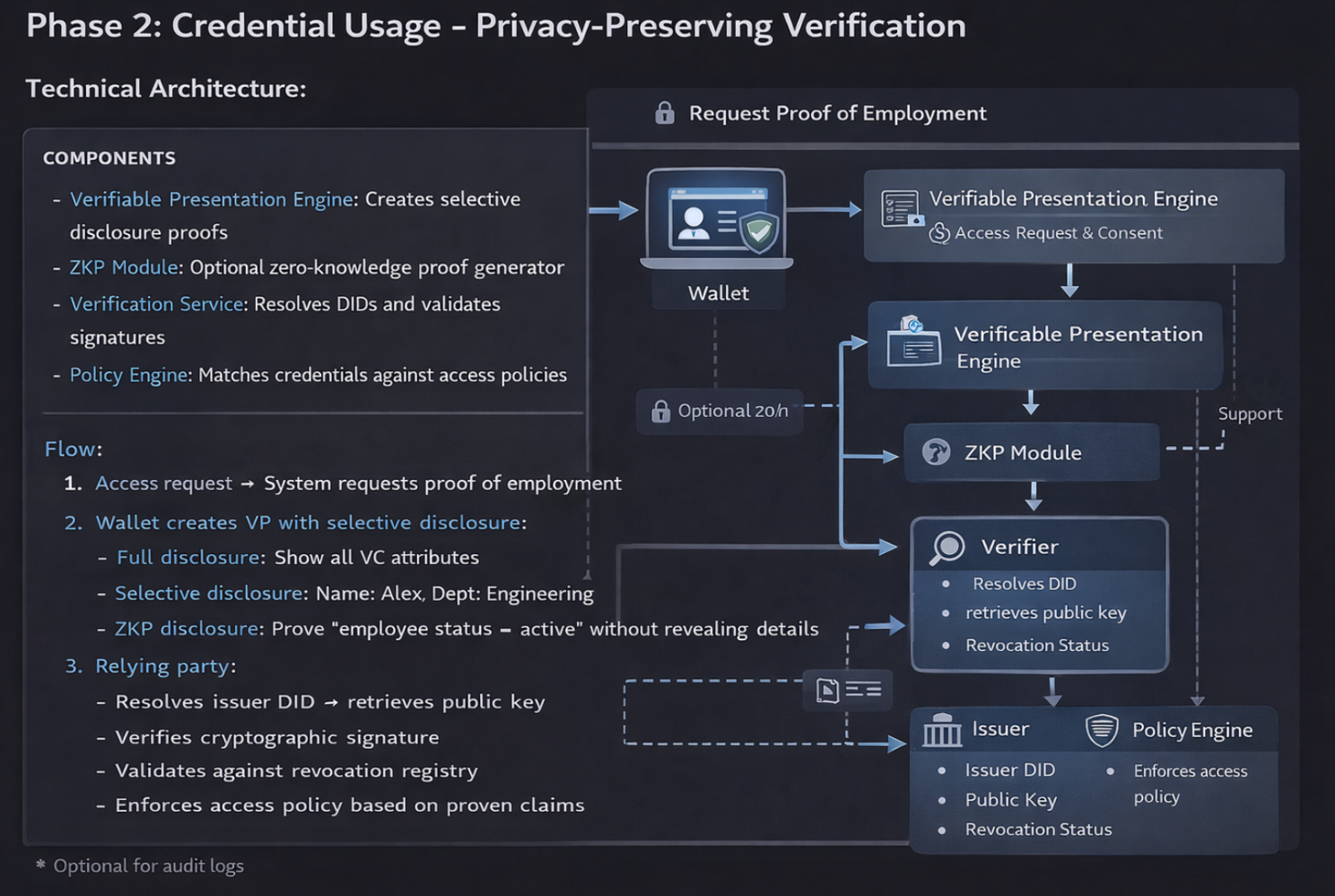
Example: Building Access with ZKP
// Employee proves they work in Engineering without revealing name
const proof = await wallet.createProof({
credentialId: 'employmentVC-123',
reveal: {}, // Nothing revealed explicitly
predicates: {
'department': { equals: 'Engineering' },
'status': { equals: 'Active' }
}
});
// System verifies proof is valid and predicates are true
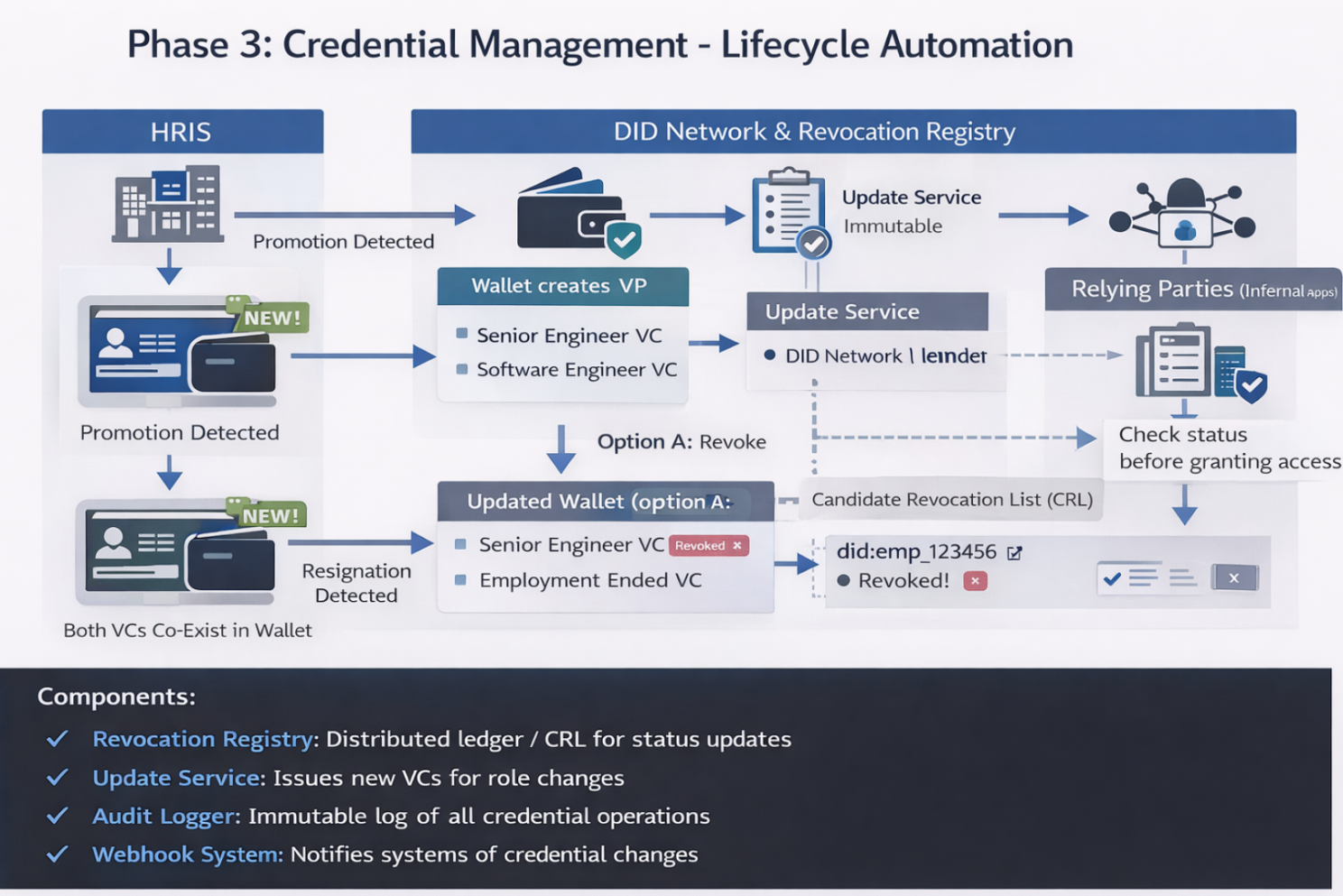
// Grants building access without knowing who exactlyPhase 3: Credential Management - Lifecycle Automation
Technical Architecture
Technical Implementation Stack
Real-World Use Cases Implemented
1. Automated Physical Access Control
Before SSI
def grant_building_access(employee_id):
hr_check = query_hr_database(employee_id) # Slow, centralized
it_check = check_ad_account(employee_id) # Separate system
security_approval = manual_form_approval() # Paper trail
# 3-5 business days processAfter SSI
def grant_building_access(vp):
if verify_vp(vp) and check_role(vp, 'Engineering'):
door_controller.grant_access() # Instant
audit_log.record(vp.did) # Privacy-preserving log2. Vendor/Contractor Management
Third-party contractors receive temporary, scoped credentials that auto-revoke on end date, eliminating forgotten accounts.
3. Multi-Company Verification
Employees moving between partner companies can prove previous employment without contacting former HR departments.
Security & Privacy Advantages
Minimal Data Exposure
Relying parties see only what's necessary
No Central Database
Eliminates single points of failure
Cryptographic Assurance
Tamper-proof credentials
User Consent
Employees control what to share
Revocation Certainty
Instant global revocation possible
Implementation Roadmap
Phase 1 (Months 1-3): Pilot Program
• Select pilot department (50-100 employees)
• Implement basic VC issuance for employee badges
• Train HR and IT teams
Phase 2 (Months 4-6): Extended Integration
• Integrate with 2-3 internal systems (email, project tools)
• Implement selective disclosure
• Develop employee wallet app
Phase 3 (Months 7-12): Full Deployment
• Organization-wide rollout
• Vendor/contractor inclusion
• Advanced features (ZKP, cross-company verification)
Challenges & Mitigations
| Challenge | Solution |
|---|---|
| Employee Adoption | Gamified training, incentives for wallet usage |
| Legacy System Integration | API adapters, gradual sunset strategy |
| Key Management | Hardware security modules, multi-sig wallets |
| Regulatory Compliance | Built-in GDPR tools, consent tracking |
| Network Choice | Hybrid approach (private ledger for internal, public for external) |
Quantifiable Benefits
Early adopters report:
70%
reduction in HR verification requests
85%
faster onboarding process
Zero
credential fraud incidents
40%
reduction in IT helpdesk tickets for access issues
Full
compliance with privacy regulations
The Future: Beyond Employment Credentials
The architecture naturally extends to:
Skills & Training Certifications
Micro-credentials for completed courses
Performance Credentials
Verifiable peer reviews and achievements
Portable Benefits
Health insurance and retirement credentials
Decentralized Organizations
DAO membership and contribution proofs
Conclusion
The transition to SSI for employee management represents more than a technological upgrade-it's a fundamental rethinking of the employer-employee relationship in the digital age.
By giving employees control over their professional identity while providing organizations with unparalleled security and efficiency, SSI creates a win-win scenario.
As shown in the architecture, the system elegantly separates concerns: HR issues, employees control, and systems verify-without unnecessary data sharing or centralized vulnerabilities.
In an era of increasing digital threats and privacy expectations, SSI isn't just innovative; it's becoming essential.
Organizations that adopt this architecture today will not only solve current identity management challenges but will also position themselves for the decentralized future of work-where identities are portable, privacy is preserved, and trust is cryptographic rather than bureaucratic.
About the Architecture
This design is based on W3C Verifiable Credentials standards, decentralized identifier specifications, and real-world implementations from early SSI adopters in enterprise environments. The architecture maintains backward compatibility with existing systems while providing a clear path toward fully decentralized identity management.
Case Studies
Empowering Digital
Evolution
Blogs
Empowering Digital
Evolution
BitViraj Technologies - Your Gateway to
Tomorrow's Innovations
Embark on a DigitalJourney


The next-generation digital technology company Bitviraj has the potential to empower and reinvent business in the current fast-paced market.
Our Service
- Website Development
- Application Development
- Blockchain Development
- Gaming and Metaverse








